Data Access Auditing | Web Scraping Tool | ScrapeStorm
Abstract:Data Access Auditing is to monitor, analyze and record the access behavior of users or systems to ensure the security, legality and compliance of data. ScrapeStormFree Download
ScrapeStorm is a powerful, no-programming, easy-to-use artificial intelligence web scraping tool.
Introduction
Data Access Auditing is to monitor, analyze and record the access behavior of users or systems to ensure the security, legality and compliance of data. Its core purpose is to control the access rights to sensitive data and ensure that only authorized personnel can view or operate specific data. At the same time, Data Access Auditing also records the access behavior so that the data access process can be traced and audited when necessary.
Applicable Scene
Continuously audit access to sensitive data to ensure that the company complies with industry laws and regulations, such as GDPR, HIPAA, etc., to prevent illegal operations and information leakage. Banks, securities companies and other institutions conduct permission audits on customer information and transaction records to ensure that internal personnel do not illegally access or tamper with data, and protect customer privacy and transaction security.
Pros: Unauthorized access and abuse of authority can be effectively discovered, and timely measures can be taken to deal with them, thereby improving overall data security. Every data access operation will be recorded in detail, making it easy to trace back when problems arise, and to identify the responsible person and the operation content.
Cons: The design and implementation requires comprehensive consideration of different systems, data sources, and user roles, and the setup is relatively complex, especially for large enterprises. Audit records themselves are also a kind of data, and long-term operation will generate a large amount of log information. Managing these logs requires additional storage and processing resources.
Legend
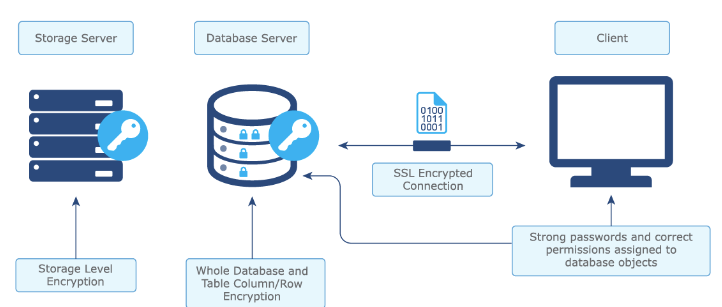
1. Protecting Data and Auditing Database Access.
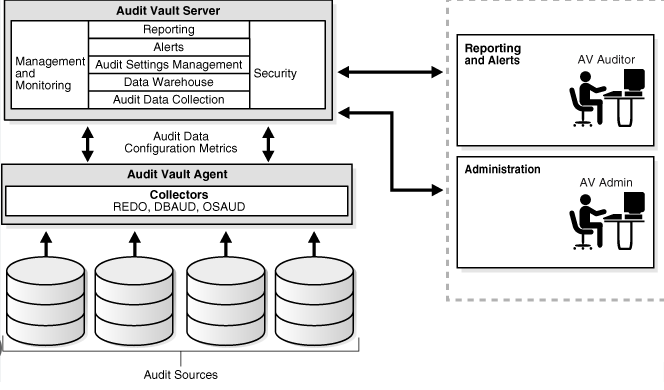
2. Database Auditing.
Related Article
Reference Link
https://developer.android.com/about/versions/11/privacy/data-access-auditing
https://www.linkedin.com/advice/0/how-do-you-monitor-audit-data-access-usage-across-1f